Haruskah Ku Lepas Mimpiku….
Akankah selalu ku rasa hal ini,,,,,
Berada dalam kebimbangan yang menyelimuti raga
Berdiri dalam ketidakpastian yang membayangi jiwa
Dan berlari dari kenyataan yang seharusnya aku terima
Ya Allah jika memang semua harapan itu tidak dapat terwujud,,,,
Berilah keikhlasan kepadaku dalam menerima apa yang menjadi kehendakMu
Berilah keikhlasan yang sebenar-benarnya ikhlas kepadaku
Ikhlas yang bukan hanya terucap oleh lisan,,
Tetapi juga ikhlas yang di amini oleh hati dan dicerminkan oleh perbuatan
Ya Allah jika memang harapan dan impian ku hanya akan melukai orang yang aku sayang
kan ku biarkan orang yang ku sayang bahagia tanpa terkekang sedikitpun oleh kehadiran ku
Kan ku biarkan orang yang ku sayang untuk mencari kebahagiaan tanpa bayang-bayang diriku
Pintaku padaMu Ya Allah,,,,,,,
Berilah ia selalu kebahagiaan dimanapun ia berada
Lindungilah ia selalu dimanapun ia berada
Dan berilah yang terbaik untuknya,,,,dan untuk hidupnya,,,
Karena ku tak ingin melihatnya bersedih
Ku hanya ingin melihatnya tersenyum bahagia bersama orang-orang yang ia sayang,,,,,,,,,
UTS bener..
duh,, salah soal tenyata..
ya udah deh,, kita benerin..
maaf ya pa..
SOAL
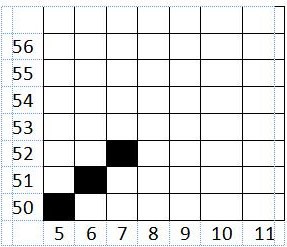
Hitung lokasi 7 titik pertama yang dilewati oleh garis (5,50) – (80,99) dengan menggunakan algoritma garis Bresenham.
Gambarkan hasil perhitungannnya!
Dik: Garis (5,50) – (80, 99)
x1 = 5
y1 = 50
x2 = 80
y2 = 99
Hitung lokasi 7 titik pertama! Kemudian, gambarkan hasil perhitungannya!
Jawab:
dx = x2 – x1 = 80 – 5 = 75
dy = y2 – y1 = 99 – 50 = 49
d1 = 2 * dy = 2 * 49 = 98
d2 = 2 * (dy – dx) = 2 * (49 – 75) = 2 * (-26) = -52

TITIK 1
e = d1 – dy
= 98 – 49
= 49
x = x1 = 5 y = y1 = 50
TITIK 2
e >= 0
49 >= 0 (benar)
Maka,
e = e + d2
= 49 + (-52)
= -3
x = x + 1
= 5 + 1
= 6
y = y + 1
= 50 + 1
= 51
y >= y2
51>= 99 (salah)
TITIK 3
e >= 0
-3 >= 0 (benar)
Maka,
e = e + d2
= (-3) + (-52)
= -55
x = x + 1
= 6 + 1
= 7
y = y + 1
= 51 + 1
= 52
y >= y2
52>= 99 (salah)
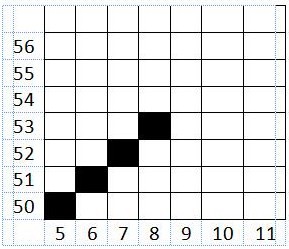
TITIK 4
e >= 0
-55 >= 0 (benar)
Maka,
e = e + d2
= (-55) + (-52)
= -107
x = x + 1
= 7 + 1
= 8
y = y + 1
=52 + 1
=53
y >= y2
53 >= 99 (salah)
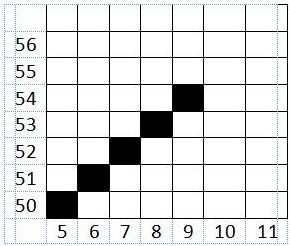
TITIK 5
e >= 0
-107>= 0 (benar)
Maka,
e = e + d2
=-107 + (-52)
= -159
x = x + 1
= 8 + 1
= 9
y = y + 1
= 53 + 1
= 54
y >= y2
54 >= 99 (salah)
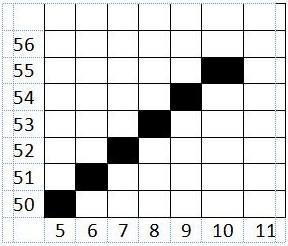
TITIK 6
e >= 0
-159>= 0 (benar)
Maka,
e = e + d2
= -159 +(-52)
= -211
x = x + 1
= 9 + 1
= 10
y = y + 1
= 54 + 1
= 55
y >= y2
55>= 99 (salah)
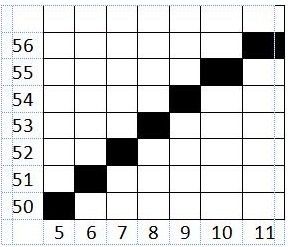
TITIK 7
e >= 0
-211 >= 0 (benar)
Maka,
e = e + d2
= -211+ (-52)
= -263
x = x + 1
= 10 + 1
= 11
y = y + 1
= 55 + 1
= 56
y >= y2
56>= 99 (salah)
Dst. Karena hanya sampai 7 titik, maka setelah titik ke-7 penghitungan dihentikan.
Program Pembentuk Garis
Garis adalah kumpulan dari titik-titik.
Kalo ga percaya coba aja baris program berikut:
unit grapika2;
interface
uses
Windows, Messages, SysUtils, Variants, Classes, Graphics, Controls, Forms,
Dialogs, StdCtrls;
type
Tprak2 = class(TForm)
Button1: TButton;
ColorDialog1: TColorDialog;
Label1: TLabel;
Label2: TLabel;
procedure Button1Click(Sender: TObject);
procedure FormCreate(Sender: TObject);
procedure FormMouseDown(Sender: TObject; Button: TMouseButton;Shift: TShiftState; X, Y: Integer);
procedure FormClose(Sender: TObject; var Action: TCloseAction);
procedure FormMouseMove(Sender: TObject; Shift: TShiftState; X,Y: Integer);
private{ Private declarations }ex,ye : integer;warna : tcolor;mulai : boolean;
public{ Public declarations }
procedure garis(x1,y1,x2,y2 : integer; w : Tcolor);
end;
var
prak2: Tprak2;
implementation
{$R *.dfm}
procedure Tprak2.garis(x1,y1,x2,y2 : integer; w : Tcolor);
var a,b,sinteta,costeta,d : real;di,r,x,y : integer;
begin
a:=x2-x1; b:=y2-y1;d:=sqrt(sqr(a)+sqr(b));
sinteta := b/d;
costeta := a/d;
di := round(d);
for r := 0 to di do
begin
x := round(x1 + r*costeta);
y := round(y1 + r*sinteta);
canvas.Pixels[x,y]:=w;
end;
end;
procedure Tprak2.Button1Click(Sender: TObject);
begin
colordialog1.execute;
warna := colordialog1.color;
end;
procedure Tprak2.FormCreate(Sender: TObject);
begin
prak2.Position := podesktopcenter;
prak2.Color := clDefault;
mulai := false;
warna := clred;
end;
procedure Tprak2.FormMouseDown(Sender: TObject; Button: TMouseButton;Shift: TShiftState; X, Y: Integer);
begin
if mulai then
garis (ex,ye,x,y,warna)
else
mulai := true;ex := x;ye := y;
end;
procedure Tprak2.FormClose(Sender: TObject; var Action: TCloseAction);
begin
// menuku.show;
prak2.Hide;
end;
end.
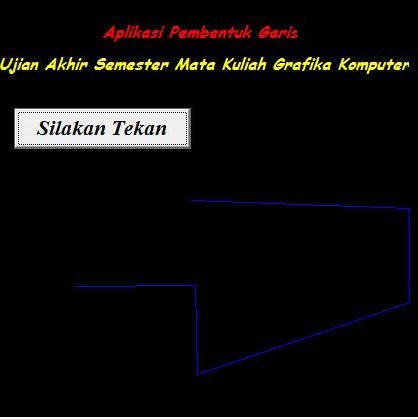
Nah, dari program berikut, jika codingnya benar, bisa kita liat hasilnya akan seperti berikut.
Selamat mencoba..
BRESENHAM
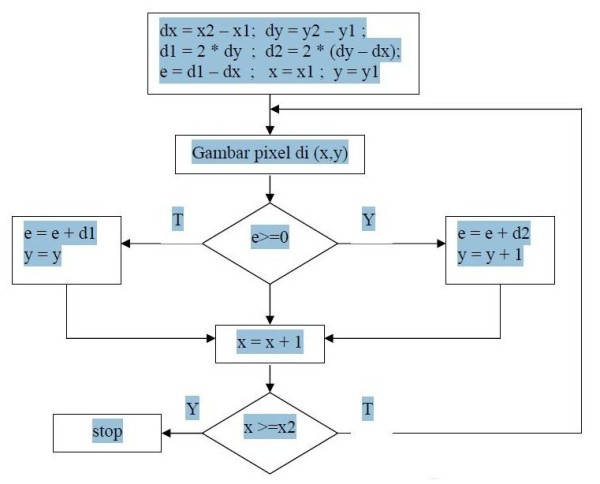
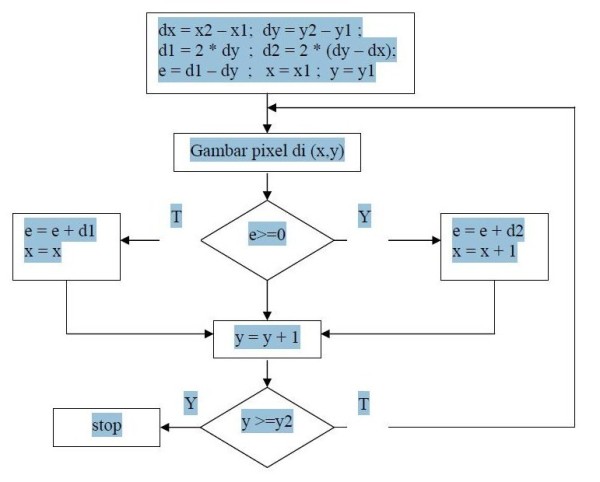
ALGORITMA GARIS BRESENHAM
- dikembangkan oleh Bresenham
- berdasarkan selisih antara garis yang diinginkan terhadap setengah ukuran dari pixel yang sedang digunakan
Algoritma Bresenham untuk dx > dy
Algoritma Bresenham untuk dx < dy
Contoh :
Hitung lokasi 7 titik pertama yang dilewati oleh garis (15,71) – (114,210) dengan menggunakan algoritma garis Bresenham. Gambarkan hasil perhitungannnya!
Dik:
Garis (15, 71) – (114, 210)
x1 = 15 y1 = 71
x2 = 114 y2 = 210
Hitung lokasi 7 titik pertama! Kemudian, gambarkan hasil perhitungannya!
Jawab:
dx = x2 – x1
= 114 – 15
= 99
dy = y2 – y1
= 210 – 71
= 139
d1 = 2 * dy
= 2 * 139
= 278
d2 = 2 * (dy – dx)
= 2 * (139 – 99)
= 2 * 40
= 80
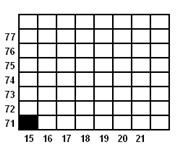
TITIK 1
e = d1 – dy
= 278 – 139
= 139
x = x1 = 15
y = y1 = 71
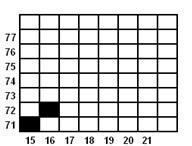
TITIK 2
e >= 0
139 >= 0 (benar)
Maka,
e = e + d2
= 139 + 80
= 219
x = x + 1
= 15 + 1 = 16
y = y + 1
= 71 + 1 = 72
y>= y2
72 >= 210 (salah)
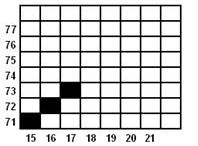
TITIK 3
e >= 0
219 >= 0 (benar)
Maka,
e = e + d2
= 219 + 80
= 299
x = x + 1
= 16 + 1
= 17
y = y + 1
= 72 + 1
= 73
y >= y2
73 >= 210 (salah)
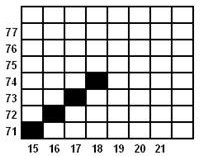
TITIK 4
e >= 0
299 >= 0 (benar)
Maka,
e = e + d2
= 299 + 80
= 379
x = x + 1
= 17 + 1
= 18
y = y + 1
= 73 + 1
= 74
y >= y2
74 >= 210 (salah)
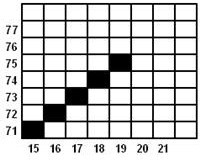
TITIK 5
e >= 0
379 >= 0 (benar)
Maka,
e = e + d2
= 379 + 80
= 459
x = x + 1
= 18 + 1
= 19
y = y + 1
= 74 + 1
= 75
y >= y2
75 >= 210 (salah)
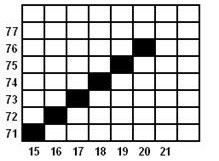
TITIK 6
e >= 0
459 >= 0 (benar)
Maka,
e = e + d2
= 459 + 80
= 539
x = x + 1
= 19 + 1
= 20
y = y + 1
= 75 + 1
= 76
y >= y2
76 >= 210 (salah)
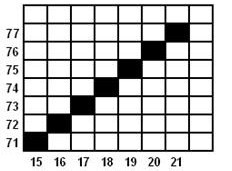
TITIK 7
e >= 0
539 >= 0 (benar)
Maka,
e = e + d2
= 539 + 80
= 619
x = x + 1
= 20 + 1
= 21
y = y + 1
= 76 + 1
= 77
y >= y2
77 >= 210 (salah)
Dst.
Karena hanya sampai 7 titik, maka setelah titik ke-7 penghitungan dihentikan.
Sejati hanya Teori
Kata “SEJATI” hanya “TEORI”
Tak ada yang sempurna di dunia ini, hanya Allah yang mempunyai seluruh kesempurnaan. Manusia selalu berusaha untuk sebuah kesempurnaan, namun itu jauh dari kenyataan. Walau mereka juga sadar akan ketidakmampuan untuk sempurna. Cinta sejati, itu teori.. kesejatian mutlak hanya untuk Allah.. kesetiaan juga mutlak untuk Allah, semua untuk Allah. Sahabat sejatipun, cuma teori. “HANYA TEORI”.
Allah telah menyadarkanku akan kesejatian. Semua butuh pengorbanan, dan sejati pun butuh pengorbanan. Hati, fikiran, jiwa raga, materi dan emosi. Yang aku ketahui, sahabat sejati itu ada dalam suka & duka, tidak cape untuk saling mengingatkan, belajar bareng hadapi semuanya, tak berani saling menyakiti, intinya menjaga hati. Sahabat sejati tak memandang suatu karakter. Karakter baik ataupun buruk, justru itu letak inti masalah dalam menjalin suatu kesejatian.
“SAHABAT”… makna ini memang terlalu berat untuk kita fahami dan kita aplikasikan dalam hidup. Tak ayal, sering kali kata “SAHABAT” ini jadi alasan untuk sebuah keegoisan. Sedikit timbul masalah, yang terbesit dalam fikiran adalah “Apa ini yang namanya sahabat?” Padahal, seharusnya pertanyaan itu tak keluar, karena persahabatan tak menuntut untuk sebuah karakter sempurna. Memang, hidup itu tidak mendapatkan kesempurnaan tapi “TERBAIK” untuk diri sendiri dan orang lain.
Friendship never die by everything in the world
poem by Irma
gelombang badai datang…
Dengan sekejap hancur leburkan apa yang di sentuh!!!
kini harapan hanya puing…
mimpi tak lagi seperti dulu…
tapi angan selalu muncul..
aku kosong….
aku sepi…
aku gundah..
diam dalam gejolak badai….
keyakinan akan sang Kholiq…
satu-satunya harapan….
tuk raih kembali apa yang hilang….
aku butuh Dia yang tuk dapat tenangkan hati….
Aku butuh Dia tuk bangun kembali puing-puing harapan yang tlah hancur….
mentari pagi cepat lah datang…
aku butuh hangat mu tuk hangatkan hati yang terasa dingin….
ups…aku ingin tak hanya hangat yang kurasa tapi juga aku ingin terasa sejuk….
wahai sang penjaga malam dan siang….
wahai sang penjaga hati….
temani aku…
dampingi aku….
tuntun aku….
tenangkan aku ….
doa ku hanya padaMu….
pintaku hanya padaMu….
syukurku hanya untuk-Mu…
tutup mataku…jika aku melihat apa yang Kau laranng..
tutup telingaku…jika aku mendengar apa yang Kau larang…
tutup hidungku… jika aku mencium apa yang Kau larang…
tapi jangan kau tutup hatiku…
cinta ku hanya untukMu….
karena Engkau sanng pemilik cinta….
maafkan aku tak sempurna taati perintahMu…
maafkan aku tak selalu jauhi laranganMu…
computer-virus-in-general
Virus Origins
Computer viruses are called viruses because they share some of the traits of biological viruses. A computer virus passes from computer to computer like a biological virus passes from person to person.
Unlike a cell, a virus has no way to reproduce by itself. Instead, a biological virus must inject its DNA into a cell. The viral DNA then uses the cell’s existing machinery to reproduce itself.
A computer virus shares some of these traits. A computer virus must piggyback on top of some other program or document in order to launch. Once it is running, it can infect other programs or documents.
People write computer viruses. A person has to write the code, test it to make sure it spreads properly and then release it. A person also designs the virus’s attack phase, whether it’s a silly message or the destruction of a hard disk.
Why do they do it?
There are at least three reasons. The first is the same psychology that drives vandals and arsonists. Why would someone want to break a window on someone’s car, paint signs on buildings or burn down a beautiful forest? For some people, that seems to be a thrill. If that sort of person knows computer programming, then he or she may funnel energy into the creation of destructive viruses.
The second reason has to do with the thrill of watching things blow up. Some people have a fascination with things like explosions and car wrecks. When you were growing up, there might have been a kid in your neighborhood who learned how to make gunpowder. And that kid probably built bigger and bigger bombs until he either got bored or did some serious damage to himself. Creating a virus is a little like that — it creates a bomb inside a computer, and the more computers that get infected the more “fun” the explosion.
The third reason involves bragging rights, or the thrill of doing it. Sort of like Mount Everest — the mountain is there, so someone is compelled to climb it. If you are a certain type of programmer who sees a security hole that could be exploited, you might simply be compelled to exploit the hole yourself before someone else beats you to it.
Of course, most virus creators seem to miss the point that they cause real damage to real people with their creations. Destroying everything on a person’s hard disk is real damage. Forcing a large company to waste thousands of hours cleaning up after a virus is real damage. Even a silly message is real damage because someone has to waste time getting rid of it. For this reason, the legal system is getting much harsher in punishing the people who create viruses.
Virus History
Traditional computer viruses were first widely seen in the late 1980s, and they came about because of several factors. The first factor was the spread of personal computers (PCs). Prior to the 1980s, home computers were nearly non-existent or they were toys. Real computers were rare, and they were locked away for use by “experts.” During the 1980s, real computers started to spread to businesses and homes because of the popularity of the IBM PC (released in 1982) and the Apple Macintosh (released in 1984). By the late 1980s, PCs were widespread in businesses, homes and college campuses.
The second factor was the use of computer bulletin boards. People could dial up a bulletin board with a modem and download programs of all types. Games were extremely popular, and so were simple word processors, spreadsheets and other productivity software. Bulletin boards led to the precursor of the virus known as the Trojan horse. A Trojan horse is a program with a cool-sounding name and description. So you download it. When you run the program, however, it does something uncool like erasing your disk. You think you are getting a neat game, but it wipes out your system. Trojan horses only hit a small number of people because they are quickly discovered, the infected programs are removed and word of the danger spreads among users.
The third factor that led to the creation of viruses was the floppy disk. In the 1980s, programs were small, and you could fit the entire operating system, a few programs and some documents onto a floppy disk or two. Many computers did not have hard disks, so when you turned on your machine it would load the operating system and everything else from the floppy disk. Virus authors took advantage of this to create the first self-replicating programs.
Early viruses were pieces of code attached to a common program like a popular game or a popular word processor. A person might download an infected game from a bulletin board and run it. A virus like this is a small piece of code embedded in a larger, legitimate program. When the user runs the legitimate program, the virus loads itself into memory and looks around to see if it can find any other programs on the disk. If it can find one, it modifies the program to add the virus’s code into the program. Then the virus launches the “real program.” The user really has no way to know that the virus ever ran. Unfortunately, the virus has now reproduced itself, so two programs are infected. The next time the user launches either of those programs, they infect other programs, and the cycle continues.
If one of the infected programs is given to another person on a floppy disk, or if it is uploaded to a bulletin board, then other programs get infected. This is how the virus spreads.
The spreading part is the infection phase of the virus. Viruses wouldn’t be so violently despised if all they did was replicate themselves. Most viruses also have a destructive attack phase where they do damage. Some sort of trigger will activate the attack phase, and the virus will then do something — anything from printing a silly message on the screen to erasing all of your data. The trigger might be a specific date, the number of times the virus has been replicated or something similar.
Virus Evolution
As virus creators became more sophisticated, they learned new tricks. One important trick was the ability to load viruses into memory so they could keep running in the background as long as the computer remained on. This gave viruses a much more effective way to replicate themselves. Another trick was the ability to infect the boot sector on floppy disks and hard disks. The boot sector is a small program that is the first part of the operating system that the computer loads. It contains a tiny program that tells the computer how to load the rest of the operating system. By putting its code in the boot sector, a virus can guarantee it is executed. It can load itself into memory immediately and run whenever the computer is on. Boot sector viruses can infect the boot sector of any floppy disk inserted in the machine, and on college campuses, where lots of people share machines, they could spread like wildfire.
In general, neither executable nor boot sector viruses are very threatening any longer. The first reason for the decline has been the huge size of today’s programs. Nearly every program you buy today comes on a compact disc. Compact discs (CDs) cannot be modified, and that makes viral infection of a CD unlikely, unless the manufacturer permits a virus to be burned onto the CD during production. The programs are so big that the only easy way to move them around is to buy the CD. People certainly can’t carry applications around on floppy disks like they did in the 1980s. Boot sector viruses have also declined because operating systems now protect the boot sector.
Infection from boot sector viruses and executable viruses is still possible. Now virus not only infect programs but also infect another files, such as document files (.doc), pictures (.png, .jpg) and music files (.mp3).
How to Protect Your Computer from Viruses
You can protect yourself against viruses with a few simple steps:
- Your Operating System (OS) has to be up-to-date
If you are truly worried about traditional (as opposed to e-mail) viruses, you should be running a more secure operating system like UNIX. You never hear about viruses on these operating systems because the security features keep viruses (and unwanted human visitors) away from your hard disk. - You should have anti-virus software installed on your system and make sure that it is updated on a daily basis to ensure that it has the latest fixes for new viruses, worms, and Trojan horses.
Make sure that your antivirus software scans emails and files as they are downloaded from the Internet - Have your firewall enabled at all times, and if you don’t have one stop whatever you’re doing, get a firewall right now and install it
If you simply avoid programs from unknown sources (like the Internet), and instead stick with commercial software purchased on CDs, you eliminate almost all of the risk from traditional viruses.
BEE competition
Waa… sudah lama ndRa tau tentang blog. But, this is my first time.. Wuih..
Well, I dont know what I want to write today. Jadi kayanya crita tentang kemarin aj deh..
Ceritanya kemarin tu ndRa les seperti biasa..
Sekedar pengumuman ndRa les di salah satu LBPP LIA Bandung.:)
Nah guru kita yang baik dan rendah hati mempertontonkankan kita film, yang kata ndRa keren banget.. Judul tu film Akeelah and the Bee. Ceritanya tentang remaja Afrika-Amerika yang hebat banget nge-spell kata. Semacam kontes/ kompetisi dimana jurinya tu ngasihin satu kata, lalu kita nge-eja/ ngucapin per kata. Waktu nonton tu film kebetulan bawa kamus, kamus saku sih, dan katanya ga ad di kamus itu. Flimnya ga tlalu lama. Keluar skitar taun 2006. Cobain deh tonton.. Hmm,, yang ndRa pikirin ada ga ya kontes kaya gitu di sini. Maksudnya tu pake bahasa Indonesia.. Kalo ad kaya gimana ya…
OOoo ya,, kalo mau nyoba spelling, klik disini aj. Lumayan lah bwat ngelatih pendengaran kita. Skalian blajar kosakata baru. In english of course..